Trendaavat aiheet
#
Bonk Eco continues to show strength amid $USELESS rally
#
Pump.fun to raise $1B token sale, traders speculating on airdrop
#
Boop.Fun leading the way with a new launchpad on Solana.

wavey
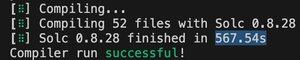
ngl, "disrupt solc" was not on my bingo card, but here we are.
check these massive gains for solx over @solidity_lang in compile time.
... and just wait till you see the gains in runtime gas + code size 👀

wavey7.8. klo 21.38
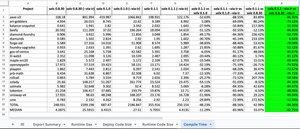
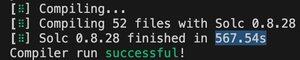
nothing but love for @solidity_lang, but via-ir compile times this long on an M1 Max processor is just crazy.
was able to get the same codebase down to < 1min on solx from @the_matter_labs
that’s a 10x improvement! great work happening over there.
2,83K
wavey kirjasi uudelleen
Aave’s $GHO stablecoin is often described as the protocol’s next big revenue driver. But when you look at the numbers, GHO is more of a loss leader
On the supply side, ~$164M of GHO is borrowed at ~5.5% APR. On the demand side, the sGHO savings token holds ~$154M and pays ~9% APY. That means the DAO brings in ~$0.75M a month in interest but pays ~$1.16M out, a net deficit of about $0.39M/month.
To keep GHO liquid, the DAO is also paying for liquidity. The GHO Liquidity Committee’s phase IV budgets allocate 650k GHO for Ethereum & 300k GHO for Arbitrum each quarter ($950k). A later proposal sought authority to spend 3.5M GHO on continuing ops.
Now, a new ‘CEX Earn’ proposal asks for 5M GHO to incentivize centralized exchange deposits and marketing. Combined, these incentive programs run into tens of millions of dollars.
Altogether, GHO is likely costing Aave near enough to $1m in negative PnL per month.
Advocates note that 1 GHO minted supposedly brings the same revenue as $10 of traditional borrowing. But that revenue isn’t materializing into a benefit for the DAO.
A revenue driver that loses money and depends on heavy subsidies isn’t sustainable. If the DAO stops these payouts, demand for GHO will drop quickly. Sustainable growth will require organic use cases and demand sinks, not endless incentives. More rational rates for borrowers and lenders seem like the logical first step
Questions for those closer to what is going on at @aave - What changes are planned to align sGHO yields with borrow rates, if any? How will GHO generate organic demand that doesn’t rely on subsidies from the DAO's warchest? Happy to learn if there’s a clear path to profitability. Maybe someone at @Token_Logic or @lemiscate will know
3,1K
incredible achievement given the circumstances. lots to be grateful for.
but @ResupplyFi is purpose-built for this era of stablecoins. strengthened by trust from users, real revenue, and an unreal community.
more to come.
motivation at all-time highs. onward!

Resupply1.8. klo 20.25
Resupply’s $10M bad debt has been paid in full.
$8.8M in bad debt associated with the recent exploit was initially paid off.
The remaining $1.13M has been covered by a loan secured from @yearnfi and will be gradually repaid using protocol revenue generated from Convex and Yearn Finance’s staked $RSUP positions.
This officially brings the last of the bad debt to zero.

1,13K
this is 2025’s most fascinating security find imo:
a "zero‑day" that hackers were quietly positioning upon, betting it'd stay hidden while the future payoff grew.
thankfully caught just in time by the good guys.
outstanding work by @deeberiroz @pcaversaccio @dedaub

sudo rm -rf --no-preserve-root /10.7.2025
It gets even more fancy: the way Etherscan was tricked showing the wrong implementation contract is based on setting 2 different proxy slots in the same frontrunning tx. So Etherscan uses a certain heuristic that incorporates different storage slots to retrieve the implementation contract.
There is an old proxy by OpenZeppelin who used the following slot: `keccak256("org.zeppelinos.proxy.implementation")` = `0x7050c9e0f4ca769c69bd3a8ef740bc37934f8e2c036e5a723fd8ee048ed3f8c3`
We now also have the standard EIP-1967 slot `bytes32(uint256(keccak256('eip1967.proxy.implementation')) - 1)` = `0x360894a13ba1a3210667c828492db98dca3e2076cc3735a920a3ca505d382bbc`
So what happened is that the old OpenZeppelin proxy slot was written to with the benign implementation address _and_ the standard EIP-1967 slot was also written to with the malicious implementation address. Since Etherscan queries first the old proxy slot, it retrieved the benign looking one first and thus displayed it.

6,06K
this is 2025’s most fascinating security find imo:
a "zero‑day" that hackers were quietly positioning upon, betting it'd stay hidden while the future payoff grew.
thankfully caught just in time by the good guys.
outstanding work by @deeberiroz @pcaversaccio @deeberiroz

sudo rm -rf --no-preserve-root /10.7.2025
It gets even more fancy: the way Etherscan was tricked showing the wrong implementation contract is based on setting 2 different proxy slots in the same frontrunning tx. So Etherscan uses a certain heuristic that incorporates different storage slots to retrieve the implementation contract.
There is an old proxy by OpenZeppelin who used the following slot: `keccak256("org.zeppelinos.proxy.implementation")` = `0x7050c9e0f4ca769c69bd3a8ef740bc37934f8e2c036e5a723fd8ee048ed3f8c3`
We now also have the standard EIP-1967 slot `bytes32(uint256(keccak256('eip1967.proxy.implementation')) - 1)` = `0x360894a13ba1a3210667c828492db98dca3e2076cc3735a920a3ca505d382bbc`
So what happened is that the old OpenZeppelin proxy slot was written to with the benign implementation address _and_ the standard EIP-1967 slot was also written to with the malicious implementation address. Since Etherscan queries first the old proxy slot, it retrieved the benign looking one first and thus displayed it.

388
Johtavat
Rankkaus
Suosikit
Ketjussa trendaava
Trendaa X:ssä
Viimeisimmät suosituimmat rahoitukset
Merkittävin