Trendaavat aiheet
#
Bonk Eco continues to show strength amid $USELESS rally
#
Pump.fun to raise $1B token sale, traders speculating on airdrop
#
Boop.Fun leading the way with a new launchpad on Solana.

0xTodd
Holder & Researcher |
Partner at @researchnothing |
Validator at @ebunker_eth |
Long Bitcoin, love the world.
MicroStrategy's latest issuance of STRC has become the largest financing for an IPO in the US this year.
The definition of STRC is quite complex, officially known as Variable Rate Series A Perpetual Extendable Preferred Stock; loosely speaking, it can be understood as a type of bond.
Initially, the issuance amount was $500 million, and it was oversubscribed by 5 times, raising $2.5 billion, surpassing the $1.7 billion historical record of Venture Global, the giant in the US natural gas energy sector, making it the largest energy IPO in US history.
Of course, oversubscription percentages are common and sound better from a marketing perspective.
However, $2.5 billion in real cash is being injected into the Bitcoin market.
For this STRC, the initial interest rate is 9%, which is about twice the US Treasury yield, making it quite attractive.
The initial face value is $90, and the future guaranteed official redemption price is $101.
Its price is designed to maintain around $100 in the long term, thus providing tax benefits on capital gains upon redemption.
In the past, MicroStrategy aimed to issue bonds with very low interest rates that could later convert into MicroStrategy stock. However, STRC cannot be converted into stock, which is why Saylor stated that issuing this stock would not dilute MicroStrategy.
Additionally, STRC has a very high priority, ranking above STRK and STRD, and only below STRF.
PS: MicroStrategy has issued too many of these financial instruments, including STRF, STRK, STRD, and now there's an additional STRC, making this priority list increasingly lengthy 😂. For more details on these financial instruments, you can refer to @xingpt's analysis.
STRC has a very strong capital preservation capability.
According to Swan Bitcoin's mention of Saylor's conference call, the dividends of these preferred stocks (including STRF, etc.) remain very safe even if Bitcoin drops by 80%; even in extreme declines of 90%-95%, dividends may theoretically be temporarily suspended but will ultimately be made up.
Moreover, STRC is prioritized over the other two, to be honest, although it's only been a few years, I can't even imagine what it would feel like for Bitcoin to drop back to $11,000 😂.
So some say that STRC is a bond with Bitcoin exposure, but I don't think so. It feels more like a kind of super wide-range dual-currency profit product. If Bitcoin rises, you get high interest; if Bitcoin crashes (-90%), you get Bitcoin.
But regardless, that man is still incredibly impressive, always able to design new plays that make new people spend money, then resonate upward, bringing new highs.


31,84K
The much-anticipated GPT-5 is finally here.
However, two new model testers interviewed by Reuters said that despite GPT-5's strong programming capabilities and ability to solve scientific and mathematical problems, they believe that the leap from GPT-4 to GPT-5 is not as big as from GPT-3 to GPT-4.
The reason for the bottleneck is not difficult to understand - there is not enough data.
There is a very imprecise but very vivid saying that GPT-4 has basically grabbed all the data that can be retrieved from the Internet during training, which has a feeling similar to reading the prosperity of the world.
Therefore, Ilya Sutskever, once chief scientist of OpenAI, said last year that although computing power is growing, the amount of data is not increasing simultaneously.
In fact, frankly speaking, the peak of a generalist AI for a long time is probably GPT-5, and the next AI companies must be expert AI.
For example, in this interview, Ram Kumar, an AI expert at OpenLedger, mentioned that many parties (such as Trust Wallet) want to integrate AI into their wallets, but they cannot directly use general-purpose models - they cannot meet specific needs and must be customized according to the scenario.
For example, Bloomberg immediately began developing BloombergGPT, which was trained on Bloomberg's vast proprietary terminals, news, enterprise data and text (totaling more than 700 billion tokens). It is precisely because of this closed corpus that it will definitely outperform general-purpose LLMs in financial tasks.
Another example is Musk's Tesla (FSD) autonomous driving, which is trained on billions of miles of fleet video/telemetry data collected by Tesla alone, which Tesla's competitors do not have. So a few days ago, Musk hinted that if he could also take local driving-related data in China, Tesla could fully clear the customs in the previous competition to understand the car emperor.
Therefore, the future AI white-hot competition must be in the expert data track, and it is definitely not enough to rely on the massive Internet ordinary data of free prostitution. Therefore, data attribution systems like OpenLedger will become the new infrastructure.
Imagine that precious data is valuable not only because it is scarce, but also because it can bring returns to the holder of the data (if you think of it as an asset), just like a house generates rent, and data should generate data rent.
Ram said in the video that Hugging Face is great, but the 90% of the dataset above is not that useful for commercial implementation.
Therefore, if you want to commercially use expert AI, you must first have a data ownership system, so that the holder of precious data can take out his precious data and let him get rewards and taste the sweetness, and then encourage more precious data holders to take it out, forming a positive cycle.
In the past, the resources of experts were valuable and unique to the privileged class, after all, the time of experts was limited. And in the AI era, what if it is expert AI? It greatly reduces marginal costs and makes it possible for ordinary people to use expert or quasi-expert services.
Looking forward to the OL mainnet launch.


Openledger5.8. klo 14.11
.@TrustWallet is now an @OpenLedgerHQ client, officially building with our tech.
Proud to support one of Web3’s most trusted wallets as it embraces verifiable AI.
Hear @Ramkumartweet and @EowynChen break it down on @therollupco.
4,88K
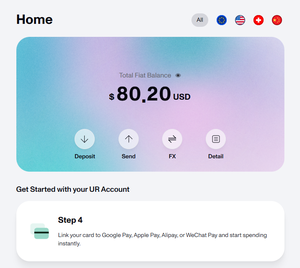
Return to an evaluation report @URNeobank
Today, another new Web3 bank was registered, a UR owned by Mantle.
After experiencing it, the overall effect is not bad:
1. Support multi-chain deposits of ETH/USDC/USDT;
2. 0.5% fee for converting crypto assets to fiat currency (can be exchanged for USD, EUR or even CNY);
3. The bottom layer is Master Card, which can be bound to google pay or Alipay.
4. KYC is required, there is currently no fee for opening an account, and 10 U😂 is also sent backwards.
After successfully opening an account, I measured the consumption, bought something casually on TB, paid 196 RMB, and the card deducted 27.4 USD, and the exchange rate was also good.
33,73K
I really didn't expect that the urban legends I have been hearing since I entered the industry:
"A man in the UK accidentally treated a hard drive containing 8,000 bitcoins as garbage"
After 12 years, it is still updated in 2025?
This time he actually wants to issue coins 🤦 ♂️
--- Dividing Line---
8,000 Bitcoins are now worth $900 million
The original PO was an engineer in Newport, the third largest city in Wales, England
He lost his hard drive with Bitcoin in 13 years, causing it to end up in a landfill.
According to the wiki, he tried various means, communicating with the city council, sending money to the people of the city, cooperating with hedge funds, hiring black box search experts, introducing robotic dogs and drones, making documentaries and even suing the city council.
This coin issuance (not that I am optimistic, just shocked), tokenized 1/5 of the Bitcoin, raised funds, and finally used the funds to buy the garbage.
In fact, I think this matter is somewhat feasible, much stronger than the previous fundraising to buy computing power to crack Satoshi Nakamoto's private key.
However, it is still unclear (1) valuation and (2) transparency.
For example, if a search expert finds it and hides it secretly, it is 8,000 bitcoins, and no one can resist this temptation.
In addition, it is not clear how the money will be spent and whether there will be obstruction from the city council.
PS: This garbage soul chicken soup picture is actually so suitable 😂🤦 ♂️ here

248E724.8. klo 23.59
For over 12 years, I tried everything to engage with Newport City Council:
•Public Proposals
•Percentages
•Mediation
•Legal action
•AND a formal £25M+ offer
$1 Billion and they ignored it all.
No response. No logic. No leadership.
They want me to give up, but
54,3K
Here's a hardcore analysis.
I used to just have a gut feeling that AAVE was the biggest, but I didn't realize that AAVE's income and interest expenses are 10x-20x those of several other competitors.
Is Compound really falling behind this obviously?


chingchalong♣️🇭🇰|𝟎𝐱𝐔4.8. klo 22.27
"An In-Depth Analysis of the Financial Statements of Leading Lending Protocols"
TL;DR
- Circular lending has become a mainstream play in DeFi, driving the fundamentals of underlying lending infrastructure platforms and eliminating lending protocols that cannot keep up with the trends.
- @eulerfinance has surged ahead with its EVK framework that allows anyone to deploy lending Vaults, leading to a significant rise in fundamentals/token prices, and the future deployment of RWA asset lending will serve as another catalyst.
- @aave has benefited from the launch of USDe + PT-USDe, the Umbrella mechanism, and the cross-chain issuance of GHO, with various metrics showing steady growth in the first half of the year.
Where do the fees for lending protocols come from?
Generally, they stem from the total interest paid on all borrowing positions, whether they are open, closed, or liquidated. This interest income will be distributed proportionally between liquidity providers and the DAO treasury.
Additionally, when a borrowing position exceeds its set LTV limit, the lending protocol will allow liquidators to execute liquidation on that position. Each type of asset corresponds to specific liquidation penalties, and the protocol will obtain the collateral and conduct auctions/fluid "liquidity liquidation" mechanisms.
What can we see from Aave's financial statements?
Aave's protocol fees and income peaked at the beginning of the year, then gradually declined alongside the market correction. I believe that the rebound in data after May is mainly due to the launch of USDe + PT-USDe, as the most significant demand for circular lending in this round is driven by Pendle's PT-type assets and the stablecoin launched by Ethena.
Data shows that in the early stages of PT-sUSDe's launch, nearly $100 million in supply was quickly deposited into the Aave market.
Moreover, the Umbrella mechanism was officially launched in June, and as of now, it has attracted approximately $300M in funds for deposit protection. At the same time, the cross-chain issuance scale of Aave's native stablecoin GHO continues to grow (current circulation ~$200M), and its multi-chain application scenarios are also expanding.
With multiple favorable factors driving it, Aave experienced a comprehensive breakthrough in July:
Net deposits surpassed $4.8 billion, ranking first in the entire network;
The protocol's net profit surged nearly 5 times month-over-month in June, reaching ~$8M;
Based on price-to-sales and price-to-earnings ratios, Aave remains an undervalued project in the sector.
Given the current growth trend and product maturity, it is expected that more traditional institutions will choose Aave as their DeFi platform. In terms of fee income, TVL, and protocol profitability, Aave is likely to continue setting new records, solidifying its position as a leader in DeFi.


86,13K
Regarding the expansion of the Ethereum mainnet, Drake made this article very clear.
If Ethereum wants to achieve a mainnet TPS of 10,000 and L2 plus millions, it needs to be updated at all three layers (execution layer, data layer, and consensus layer).
1. Execution layer: Gradually replace the old EVM with EVM 2.0, which is the Risc-V mentioned earlier, which you can understand as a very low-level design similar to Intel CPUs.
2. Data layer: Make blobs better and cheaper, helping L2 increase funding.
3. Consensus layer: Replace it with a new beacon chain, that is, beam chain, which can resist quantum, ZK, support 1 ETH staking, fast block confirmation, etc., which can be regarded as solving all current technical debts in one go.
These three layers have been improved at the same time, and together they are called the Ethereum Lean ETH project, and there is now a public worksheet to see how these major updates are progressing.
Overall, however, these workloads are enormous, and some results will not be seen until at least 2027.



Justin Drake1.8. klo 01.57
Yesterday Ethereum turned 10. Today, lean Ethereum is unveiled as a vision—and personal mission—for the next 10 years.
We stand at the dawn of a new era. Millions of TPS. Quantum adversaries. How does Ethereum marry extreme performance with uncompromising security and decentralization?
TLDR: next-generation cryptography is central to winning both offense and defense.
Disclaimer: This is a Drake take™ aimed at a broad audience. A technical deep dive into hash-based post-quantum signatures and SNARKs will follow. A healthy diversity of views across Protocol, the EF, and the broader Ethereum community is expected and welcome. It strengthens us.
defense—fort mode
Ethereum is special. 100% uptime since genesis. Unrivaled client diversity. $130B in economic security (35.7M ETH staked × $3.7K)—maybe soon $1T.
Ethereum is poised to become the bedrock of the internet of value, securing hundreds of trillions over decades, even centuries.
Ethereum must survive anything: nation states, quantum computers. Whatever comes. Call it fort mode. If the internet is up, Ethereum is up. If the world is online, the world is onchain.
offense—beast mode
Ethereum is hungry. “Scale L1, scale blobs” is a strategic urgency inside the EF’s Protocol cluster. Expect low-hanging performance gains over the next 6–12 months.
Longer term? Think gigagas L1, teragas L2. Call it beast mode.
→ 1 gigagas/sec on L1: 10K TPS, ambitious vertical scale
→ 1 teragas/sec on L2: 1M TPS, sprawling horizontal scale
Scale vs decentralization? Why not both. The moon math we need is now tamed:
→ real-time zkVMs for lean execution
→ data availability sampling (DAS) for lean data
A delicious cherry on top: full chain verification across every browser, wallet, phone.
lean upgrades
Lean Ethereum proposes bold upgrades across all three L1 sublayers:
→ lean consensus is beacon chain 2.0: hardened for ultimate security and decentralization, plus finality in seconds; formerly branded as “beam chain”
→ lean data is blobs 2.0: post-quantum blobs, plus granular blob sizing for a calldata-like developer experience
→ lean execution is EVM 2.0: a minimal, SNARK-friendly instruction set (possibly RISC-V; pronounced “risk five”), boosting performance while preserving EVM compatibility and its network effects
The consensus layer (CL), data layer (DL), execution layer (EL) have each been reimagined from first principles. Together, they unlock fort mode and beast mode.
The goal: performance abundance under the constraint of non-negotiable continuity, maximum hardness, and refreshing simplicity.
lean cryptography
Hash-based cryptography is emerging as the ideal foundation for lean Ethereum. It offers a compelling, unified answer to two megatrends reshaping the ecosystem:
→ the explosive rise of SNARKs
→ the looming quantum threat
Imagine the leanest cryptographic brick—the hash function—singlehandedly powering L1:
→ CL: hash-based aggregate signatures upgrade BLS signatures
→ DL: hash-based DAS commitments upgrade KZG commitments
→ EL: hash-based real-time zkVMs upgrade EVM re-execution
A cryptographic jewel in each of lean CL, lean DL, lean EL.
lean craft
Lean Ethereum is more than a blueprint for hardening and scaling Ethereum. More than just doubling down on security, decentralisation, and cutting-edge cryptography. It is an aesthetic. An art form. A craft. Think Jiro in Dreams of Sushi. When we can go the extra mile, we do.
Minimalism. Modularity. Encapsulated complexity. Formal verification. Provable security. Provable optimality. These are subtle yet important technical considerations. Stay tuned for the post on post-quantum cryptography that will make them explicit.
lean legacy
After 10 fantastic years, lean Ethereum is a generational oath. To keep Ethereum online no matter what. To scale it without compromise. To make it worthy of those who come next.
This is about legacy. We are builders, we are missionaries. We are Ethereum. I hope you join us.
35,84K
Amber Heard: Ah, Musk still likes angel cosplay.

Elon Musk4.8. klo 09.15
Imagine with @Grok
4,38K
Happy Ethereum 10th Birthday!
PS: V God likes shirtless + beard more and more

Mira (3/3)30.7.2025
happy 10th birthday, @ethereum!
7,58K
I saw buying a cold wallet in a small e-commerce store yesterday
As a result, the post was looted
It's really emotional
The tutorial for this post is well written
It is worth reading

最爱吃兽奶的兔🐰16.6.2025
Be careful that your assets are running naked
Not your keys, not your coins😶
The old people in the currency circle often say that "if you don't have your own private key, then these assets don't really belong to you", and security is even more on this basis.
The incident of "Douyin bought a cold wallet of 50 million yuan was stolen overnight" once again reminds everyone that safety is the most important part on the road to prosperity.
Today, Rabbit Sangui will introduce the "source pass" and "use pass" of the wallet, and discuss how to protect the security of our wallet.
1⃣ Be sure to close the source before buying
1. Never buy from unofficial channels, only from the official website or from the official list of authorized dealers.
For example, the so-called "brand new, unopened" or "special price flash sale" hardware wallets in many unauthorized third-party e-commerce channels are likely to be cracked and implanted in the backdoor of the device, and must not be touched!
2. Check the integrity of the sealing film and tamper-evident seal when receiving, and reject it decisively if it is found to be abnormal.
Don't use equipment with incomplete packaging if you don't want to return it for a momentary convenience.
At the same time, even if the packaging is intact, it may be that it has been repackaged during transportation, and some high-imitation devices have similar appearances, but the internal chips and random number generators cannot guarantee safety or have a back door.
So be sure to follow the official verification process to check the authenticity of your wallet!
Before, a group of friends came up with a cold wallet for Rabbit Sangui, and Rabbit Sangui directly refused, and he must be responsible for his own assets and refuse the second-hand wallet.
3. When you first boot up, let the wallet run off the network, and be sure to generate a mnemonic phrase in an offline environment.
At the same time, please use paper or metal plates to record the mnemonic phrase, and do not take photos, screenshots, cloud backups, etc.
The emphasis on "the build phase must be offline" is because 👇
The private key/mnemonic phrase is the only chance to be "visible & tamperable" at this moment. Although it is possible to plug in the USB in the future, it is very difficult for an attacker to read or affect the private key.
After that, if you want to do bad things with USB in the later stages, you will encounter a lot of resistance 👇
✅ Hardware ACL protection
(1) Want the device to spit out the private key? Instructions do not exist and do not spit out
(2) Want to secretly read internal Flash? The address is not on the whitelist and cannot be read
✅ Firmware signature protection
(1) If a hacker wants to flash a new firmware with a backdoor, they must spoof the vendor's private key (mathematically impossible).
Forging signatures requires an exhaustive 2 to the 256th power of the key or cracking a discrete logarithm (both of which are beyond the power of modern and predictable computing)
(2) Any unsigned code pushed by BadUSB (malicious) will be rejected by the bootloader.
The bootloader is the earliest line of defense for our device to boot, and it is burned into read-only or write-protected Flash, which cannot be overwritten by the back-flashed firmware (the bootloader verifies the firmware signature with the manufacturer's public key).
✅ PIN lock protection (with self-destruct/delay policy)
(1) Even if the attacker gets the physical object, he needs to guess the PIN correctly before he can invoke the signature command.
(2) Brute-force attacks will be delayed or directly erased, which is equivalent to "private key burning".
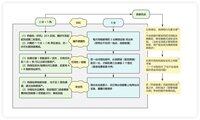
In addition to being sure to control the "source" before purchasing, you should also pay attention to safety during use.
2⃣ Precautions for daily use
1. Prevent man-in-the-middle attacks from address tampering.
For example, when transferring money, check the address information one by one on the device screen, and do not try to compare only the last few digits to prevent the clipboard from being tampered with.
2. Connect to a secure device (e.g. upgrade ROM, sign, etc.) for daily use, and disconnect immediately after completion.
3. Hot wallets only hold small amounts of funds, and large amounts are stored in cold wallets, and do not concentrate all funds on one device.
It is also what we often say: don't put your eggs in one basket~
4. Verify the mnemonic phrase regularly to confirm that the backup is available.
5. Large assets can use 2-of-3 hardware multi-signature
Similar to wanting to open a door, you need to use any 2 of the 3 keys, which not only improves the ability to resist attacks, but also retains a certain amount of redundancy.
(For example, 2 cold wallets + 1 hot wallet, assuming that the cold wallet is A, B, and the hot wallet is C)
Such benefits are as follows 👇
(1) If hot wallet C is compromised by hackers, cold wallet A + cold wallet B can still prevent the funds from being transferred.
(2) In case cold wallet A is broken, as long as cold wallet B + hot wallet C are still there, you can get back the assets.
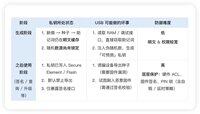
Some friends may ask, what about my three cold wallets? Here is a brief comparison of the advantages and disadvantages 👇 of "2 cold, 1 hot" and "3 cold".
6. Cold wallets and mnemonic phrases are stored in different locations (multi-location disaster recovery, avoiding one-pot ends)
#加密安全 #硬件钱包
Finally, as the cliché goes, if you don't have your own private keys, then these assets don't really belong to you, and safe use is built on this foundation!
If you have other experience, please leave a message to add it 🥰
5,2K
Johtavat
Rankkaus
Suosikit
Ketjussa trendaava
Trendaa X:ssä
Viimeisimmät suosituimmat rahoitukset
Merkittävin