Trendaavat aiheet
#
Bonk Eco continues to show strength amid $USELESS rally
#
Pump.fun to raise $1B token sale, traders speculating on airdrop
#
Boop.Fun leading the way with a new launchpad on Solana.

rusowsky
Aspiring crypto dev. Let’s ship @ithacaxyz ⛵️
rusowsky kirjasi uudelleen
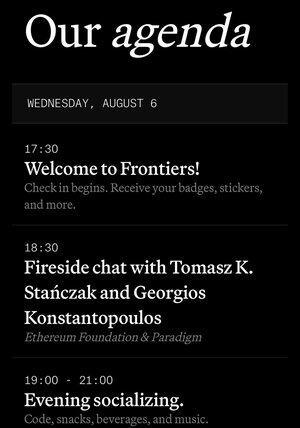
GM everybody!
Today is the first day of Frontiers, our annual open source conference for application and infrastructure devs.
We kick off with me interviewing @tkstanczak, co executive director of the Ethereum Foundation about..Ethereum!
We start at 6:30p sharp. See you there!
29,99K
rusowsky kirjasi uudelleen
it's as clear as day. the age of the cypherpunk is squarely here. the battle lines
Goliath, the Authoritarian AI Surveillance State
VS
David, who dares to challenge Goliath with a small, clever weapon (cryptography) and with courage and nothing left to lose
WE CAN AND MUST WIN
1,03K
rusowsky kirjasi uudelleen
It’s worth your time to learn these programming languages, even if you don’t use them:
1/6
C
C is on step removed from writing assembly. It forces you to understand the difference between “stack” and “heap.” You also must tangle with pointers — and training your brain to handle indirection will help you grok harder problems later as nearly every “hard” problem must be modeled with some level of indirection.
10,72K
rusowsky kirjasi uudelleen
So someone contacts you on LinkedIn with a promising job opportunity. Sounds nice, innit? They seem legit (after checking them for 1 min) and after some short convo they send you a GitHub repo with a simple Next.js "recruiting task". You clone it, run it… and 10 mins later, your device is fully compromised as you find out that your hot wallets were drained. Ok, what happened? Given the fact that we (= SEAL 911) have seen this attack over and over again, let me disclose some of the most important details:
- first, the most important caveat: do NOT run random code some random dude sent you. Honestly, fucking don't.
- check always the _executable_ config files of the repos thoroughly. In this particular case, the `next.config.js` file had a large padding hiding the malicious payload far to the right.
- always scroll horizontally - just because you don't see anything malicious when you look at the content doesn't mean it's clean.
Important: Malicious code can be hidden within files you trust, just not where you expect it.
I really hope this tweet reaches enough people to prevent at least a few future victims from falling for this kind of attack.



34,53K
Johtavat
Rankkaus
Suosikit
Ketjussa trendaava
Trendaa X:ssä
Viimeisimmät suosituimmat rahoitukset
Merkittävin


















